Comprehensive Cybersecurity Solutions for Businesses
Expertise in Governance, Risk Management, Compliance, and Incident Response.
Trusted by Leading Organizations Globally
★★★★★
Empowering Cybersecurity Excellence
At The GRC Team , we specialize in governance, risk management, and compliance, ensuring robust cybersecurity programs and effective incident response management for our clients.
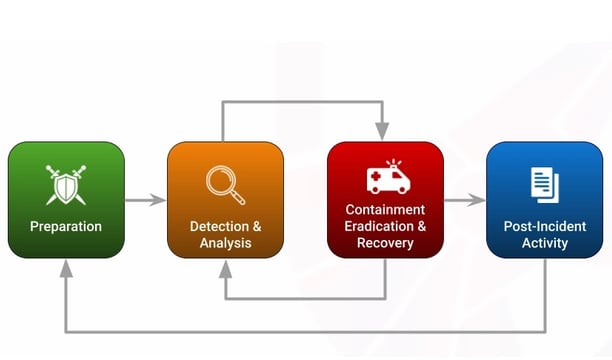




Your Cybersecurity Partner
Our team is dedicated to building comprehensive cybersecurity strategies, helping businesses navigate risks and maintain compliance in an ever-evolving digital landscape.
Cybersecurity Services
Expert solutions for governance, risk management, and compliance tailored to your business needs.
Cybersecurity Program Design


Building robust cybersecurity frameworks to protect your organization from threats.




Incident Response Management
Swift and effective response strategies to mitigate cybersecurity incidents and minimize impact.
Comprehensive Risk Assessment
Identify vulnerabilities and strengthen your organization’s security posture through thorough assessments.

Cyber Governance transformed our security approach, providing exceptional guidance in risk management and compliance strategies.
John Doe

Their expertise in incident response management has been invaluable for our organization’s cybersecurity resilience and compliance.
Jane Smith

★★★★★
★★★★★
Cybersecurity Projects
Explore our comprehensive cybersecurity solutions for governance and compliance.


Risk Management Solutions
Our risk management solutions help businesses identify, assess, and mitigate potential cybersecurity threats effectively and efficiently, ensuring compliance with industry standards and regulations.


Incident Response
We provide expert incident response services to help organizations quickly recover from cybersecurity breaches, minimizing damage and ensuring business continuity through strategic planning and execution.
